Cybersecurity
Shadow Breach: Canadian Regulators Sound Alarm Over Mounting Cyber Threats to Government Databases

Ottawa, ON —
July 28, 2025 — In a startling joint statement issued early Monday morning, two newly formed Canadian regulatory agencies — the Federal Office of Data Integrity (FODI) and the Cybersecurity Oversight Commission of Canada (COCC) — have warned that government databases across the country are “at imminent risk of sustained cyber attacks,” calling on all public sector agencies to enact immediate lockdown protocols and data segmentation strategies.
The warning follows what sources within the agencies are calling a “coordinated probing campaign” against multiple provincial and federal information systems, including health, immigration, and tax data repositories. While no breaches have yet been confirmed publicly, both regulators stress the threat is “well past theoretical.”
“Over the last 72 hours, we’ve observed an unusually high volume of anomalous behavior targeting intergovernmental data corridors,” said Marcia Denault, interim chair of COCC. “This is not a drill, and it’s not a test of the emergency broadcast system. It’s a targeted wave. We believe state-aligned actors are testing our perimeter — and they are finding gaps.”
According to a leaked FODI memo reviewed by The Canadian Sentinel, attackers are believed to be exploiting legacy authentication systems and under-patched middleware components within shared provincial-federal data pools. In particular, the memo names the National Unified Record Exchange (NURE) — a cross-ministry database that handles everything from criminal records to real estate permits — as a primary target.
FODI Commissioner Rohit Mallick issued a stark appeal to federal CIOs: “The era of slow patch cycles and unencrypted backups is over. If we don’t seal the vault, we’re handing over the keys.”
As part of its emergency response plan, the COCC has proposed activating Operation Blackroot, a classified rapid-redeployment protocol that would temporarily re-route sensitive data traffic through hardened nodes operated by the Canadian Shield Intelligence Network (CSIN) — a quasi-military agency originally designed to monitor foreign espionage.
Several municipalities have already responded. The City of Hamilton announced a 72-hour “data access freeze” on all interdepartmental transfers, while Alberta’s digital services office confirmed it has disconnected five internal portals from the national grid “out of an abundance of caution.”
Still, critics argue that Canada’s digital infrastructure has long been ill-prepared for this kind of pressure. Dr. Leanne Fraser, a former cybersecurity advisor to Public Safety Canada, said the regulatory response is overdue. “For years we’ve warned that patching wasn’t just a task — it was policy. Now they’re playing catch-up with an opponent who’s already halfway through the vault.”
Neither the RCMP nor the Office of the Privacy Commissioner of Canada has issued comment, though sources suggest a coordinated federal briefing may be underway.
As the nation braces for a potential breach, regulators are urging the public to avoid speculative panic and to trust that, “for now,” personal data remains secure. But as one anonymous FODI analyst said off-record, “We’re not afraid of the breach — we’re afraid of what happens five minutes after.”
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
Cybersecurity
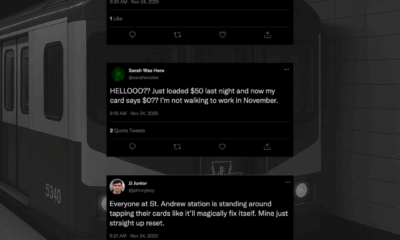
Fake QR Codes Targeting GTA Transit Riders

TORONTO, ON —
Commuters across the Greater Toronto Area are being urged not to scan a series of unauthorized QR codes that have appeared in and around multiple STS Transit stations this week. The posters, designed to look like official transit communications, promise “real-time train routing” amid ongoing service instability but cybersecurity experts say the codes actually redirect users to a malicious app that harvests personal data.
The flyers began appearing late Tuesday evening at stations in Toronto, Mississauga, Brampton, and Scarborough. Many were placed near ticket machines, station entrances, and shelters along busy commuter corridors. Their design closely mimics the colour scheme and typography of siberX Transit Systems (STS), making them nearly indistinguishable from legitimate service notices.
Security analysts consulted by ODTN say the QR codes lead to a third-party website prompting users to download an app claiming to provide “accurate route paths” during the city’s ongoing transit disruptions.
Once installed, the app immediately requests extensive device permissions — including access to contacts, location, notifications, and in some cases, stored passwords.
“This is deliberate social engineering,” said cybersecurity researcher Dr. Lena Harcourt.
“Attackers are exploiting a moment of public confusion by offering what appears to be a helpful tool. In reality, it’s a data siphon.”
Preliminary analysis shows the app transmits user information to servers registered offshore. Investigators believe the operation is linked to a broader pattern of opportunistic cyber activity that has emerged since the STS outage began.
Several commuters told ODTN they scanned the code assuming it was part of STS’s interim communication strategy.
“It looked real — same colours, same layout,” said one Brampton commuter.
“We’re all desperate for accurate info right now. That’s why people fall for this.”
Others reported seeing younger riders handing out cut flyers outside stations last night, though it remains unclear whether those individuals were aware of the scam.
STS issued a statement early Wednesday condemning the unauthorized signage and urging riders not to scan any QR codes found outside official channels.
“STS does not distribute routing information through QR posters,” the agency’s statement read.
“These materials are fraudulent and are currently under investigation.”
The incident adds another layer of complexity to a transit system already grappling with conflicting service alerts, communication failures, and worsening public mistrust.
“Criminal actors know when a city is vulnerable,” said Harcourt.
“Every gap in information becomes an opportunity for exploitation.”
Authorities are urging anyone who downloaded the suspicious app to delete it immediately, perform a device security scan, and monitor accounts for unusual activity.
What Riders Should Do
-
Do not scan any transit-related QR codes found outside official STS channels.
-
Confirm updates only through the official STS app, website, or verified social media accounts.
-
Report suspicious posters to station staff or authorities.
-
Remove any unknown app installed after scanning a QR code.
ODTN will update this story as more details become available.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
Cybersecurity
Insider Leak at SouthPort Cyber Defence Exposes Emerging Cybercrime Coalition

December 2, 2025 — A Toronto-based cybersecurity firm, Southport Cyber Defence, is under intense scrutiny tonight after confirming that an internal employee leaked sensitive system screenshots to a shadowy cybercrime gang calling itself the Crimson Harbor Collective.
The incident, while contained, has raised broader concerns across Canada’s digital infrastructure community as investigators warn that several smaller threat groups appear to be joining forces under a single coordinated movement.
Southport Cyber Defence is known for providing monitoring tools and vulnerability dashboards used by municipalities, transit agencies, and several energy-sector clients. The company confirmed in a brief statement that a junior analyst was dismissed after internal logs revealed unauthorized access to administrative panels.
Initial forensics show the employee was approached via an encrypted messaging channel and paid in cryptocurrency to capture discreet screenshots of upcoming patch schedules, SOC alert queues, and threat-correlation dashboards.
Though SouthPort insists core systems were not compromised, the leak has nonetheless prompted a federal inquiry.
Cyber intelligence sources describe the Crimson Harbor Collective as a newly surfaced operation blending members and tactics from at least three known cybercrime crews:
- GhostMire Syndicate, a ransomware group linked to attacks on U.S.–Canada logistics networks
- Silent Quay, known for telecom breaches and mass SMS spoofing
- Loomis Circle, an extortion group specializing in deepfake-based impersonation schemes
Investigators believe these groups have begun centralizing their resources, sharing stolen credentials, exchanging insider-recruitment playbooks, and coordinating target selection.
This emerging alignment is being referred to internally as “The Convergence Wave” — a trend where once-independent cybercrime actors merge into a single, multi-vector threat ecosystem.
Early signals suggest that the Crimson Harbor Collective has established communication channels, operational divisions, and shared financial infrastructure. Analysts warn that such consolidation could multiply attack capabilities across:
- municipal services
- transit and mobility sectors
- supply chain and warehousing
- provincial and federal digital platforms
The insider leak at SouthPort is believed to be part of a broader recruitment strategy targeted at individuals with access to high-value data streams, especially within cities and critical infrastructure operators.
Federal officials are now assessing whether the Crimson Harbor Collective represents a new category of threat actor — one capable of orchestrating simultaneous disruptions across sectors traditionally considered unrelated.
“This isn’t a gang. It’s a movement,” one national cybersecurity advisor told ODTN News under condition of anonymity. “These groups are no longer competing. They’re collaborating…and that changes the landscape entirely.”
As investigations continue, SouthPort Digital Defence says it has implemented additional internal controls and is cooperating fully with authorities.
Meanwhile, cybersecurity leaders warn that the real story may not be the insider leak itself, but the formation of a unified cybercrime network operating with unprecedented coordination, funding, and strategic intent.
ODTN News will continue monitoring developments as new information emerges about the Crimson Harbor Collective and the growing coalition behind it.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
Cybersecurity
Transit Screens Flash “TAKEOVER INCOMING,” Prompting Brief Panic Across Toronto

TORONTO, ON —
November 17, 2025 — Toronto commuters were startled this morning when digital screens at several bus and train terminals suddenly displayed the phrase “TAKEOVER INCOMING” before flickering off. The message appeared citywide and remained visible for approximately 30 seconds, long enough to trigger confusion and brief panic among riders trying to get to work.
Reports came in from Union Station, Bloor-Yonge, St. George, and multiple streetcar hubs where commuters were seen backing away from platforms, hesitating to board vehicles, and crowding near exits. Some riders described the moment as “unnerving,” citing the message’s abrupt appearance and ominous wording.
siberX Transit Systems (STS) quickly issued a statement downplaying the event, calling it a “momentary visual glitch”and insisting that all systems remained stable throughout the incident. STS emphasized that no service interruptions occurred and that there was “no evidence of a breach or external interference.”
“We want to reassure the public that operations are running normally,” the statement read. “This appears to be a display malfunction, and we are reviewing the logs to confirm the cause.”
Despite the calm messaging from STS, cybersecurity specialists tell ODTN News that any synchronized system abnormality, especially across multiple stations, warrants a closer look. One expert noted that even a brief, unexplained message suggests that either a central display controller malfunctioned or an unauthorized process momentarily pushed content to the screens.
City officials have requested a full technical review but have not issued further comment.
For now, transit continues to operate without interruption. Still, many riders remain uneasy, and social media is circulating photos and videos of the anomaly as the investigation unfolds.
ODTN News will continue tracking this incident and provide updates as more information becomes available.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
-
 Public5 months ago
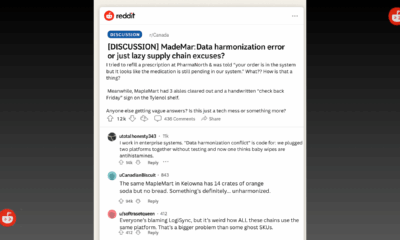
Public5 months agoReddit Thread Over ‘Inventory Drift’ Surges as Canadians Vent Over Retail Glitches
-

 Retail Watch4 months ago
Retail Watch4 months agoCalgary Small Business Hit by Sudden Payment Outage, Sparks Cybersecurity Concerns
-

 Cybersecurity6 months ago
Cybersecurity6 months agoCanadian Airline NorthSky Faces Cyberattack, Disrupting Online Services
-

 Business8 months ago
Business8 months agoCanadian Software Vendor Breach Exposes Cloud Environments Across Energy Sector
-

 Retail Watch5 months ago
Retail Watch5 months agoUnderstaffed and overwhelmed, IT teams face rising pressure as retail digitization accelerates
-

 Business5 months ago
Business5 months agoAre Canadian Companies Learning from Global Cyber Attacks? Insider Insights into the Secret Downfall of Canadian Businesses
-

 Politics4 months ago
Politics4 months agoNationwide Government System Outage Paralyzes Public Services
-

 Business4 months ago
Business4 months agoInsurance Without a Safety Net? Canadian Firms Face Premium Hikes Amid Cyber Liability Crisis